Créer des politiques d'accès
Les autorisations suivantes :
- Autorisation > politique > Toutes les autorisations
- Autorisation > politique > Ajouter
- Autorisation > politique > Supprimer
- Autorisation > politique > Visualisation
La mise en place de l'organisation suivante :
- Assurez-vous que vous avez activé le paramètre Enable Attribute Based Access Control pour votre organisation afin d'appliquer des stratégies d'accès aux utilisateurs.
Vous pouvez créer une nouvelle politique d'accès à partir de zéro en utilisant l'option Create Policy ou utiliser un modèle de politique préconstruit conçu par Genesys Cloud, le modifier et l'enregistrer en tant que politique.
Créer une politique d'accès à partir d'un modèle prédéfini
Pour créer une politique d'accès à partir d'un modèle de politique existant, procédez comme suit :
- Cliquez sur Admin.
- Sous People & Permissions, cliquez sur Access Policies.
- Cliquez sur Menu > Gestion des utilisateurs > Politiques d'accès.
- Cliquez sur Templates.
- Sélectionnez un modèle existant. Actuellement, Genesys Cloud fournit les modèles de politique d'accès suivants pour vous permettre de commencer :
- Cliquez sur le modèle de politique qui vous convient. Les détails du modèle apparaissent.
- Modifiez le nom et la description de la politique.
- Modifiez les champs domaine, entité et action si vous spécifiez une cible différente pour la politique.
- (Facultatif) Autoriser l'activation immédiate de la politique en désactivant l'option Enable Policy. Vous pouvez également activer une politique ultérieurement en la modifiant. Pour plus d'informations, voir Activer la politique d'accès.
- Modifiez les sections sujet, effet et condition dans le JSON de la politique, si nécessaire, pour répondre aux besoins de votre organisation.Remarque :
- Pour plus d'informations sur les champs utilisés dans le JSON de la politique, voir la section Définitions utilisées dans ABAC.
- Pour plus d'informations sur la liste des attributs prédéfinis utilisés dans le JSON de la politique, voir Liste des valeurs des champs restreints.
- Pour plus d'informations sur les attributs de la politique d'accès, voir Contrôle d'accès basé sur les attributs.
- Pour valider la syntaxe JSON, cliquez sur Validate Syntax dans l'onglet Validate Syntax. Corrigez les éventuelles erreurs de syntaxe et procédez à l'enregistrement de la politique. Si vous ne validez pas la syntaxe explicitement, Genesys Cloud la valide automatiquement lorsque vous enregistrez la politique. L'étape de validation syntaxique valide les éléments suivants :
- Si les champs obligatoires sont disponibles.
- Les attributs énumérés sont valables pour la cible spécifiée.
- Toutes les comparaisons d'attributs sont valables pour leurs types de données respectifs.
- Les noms d'attributs prédéfinis n'entrent pas en conflit avec ceux définis dans le système.
- Cliquez sur Save as Policy.
- Pour vérifier si la politique fonctionne comme prévu, cliquez sur l'onglet Test Policy et fournissez un échantillon de données, puis cliquez sur Test Policy.
- Pour revenir à la page des politiques, cliquez sur Annuler.
Exemples de modèles préconstruits
Actuellement, Genesys Cloud comprend les modèles de politique d'accès suivants :
Vous pouvez modifier les paramètres du modèle dans le JSON de la politique : les champs domaine, entité et action spécifient la cible ou le groupe d'appels à l'API.
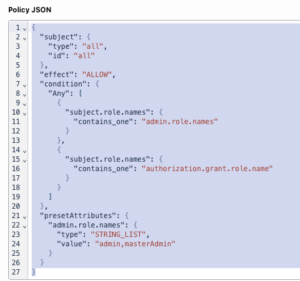
Ce modèle est soumis aux deux conditions suivantes :
Condition 1
"subject.role.names": {
"contains_one": "admin.role.names"
}
Cette condition vérifie si le sujet a un rôle d'administrateur. Si le sujet a un rôle d'administrateur, le résultat est Autoriser.
Condition 2
"subject.role.names": {
"contains_one": "authorization.grant.role.name"
}
Si le sujet n'a pas de rôle d'administrateur, l'action n'est autorisée que si le sujet a déjà le rôle qu'il essaie d'attribuer. authorization.grant.role.name est un attribut qui contient le nom du rôle que le sujet essaie d'attribuer à lui-même ou à un autre utilisateur. Ainsi, par exemple, si le sujet a un rôle de superviseur mais pas un rôle d'administrateur, le résultat est Refusé, s'il tente d'accorder un rôle d'administrateur. Dans ce scénario, le rôle d'administrateur ne figure pas dans la liste des noms de rôles des sujets.
Dans ce modèle, les attributs prédéfinis pour admin.role.names peuvent être une liste contenant les rôles admin et masterAdmin. Si vous avez d'autres rôles d'administrateur personnalisés dans votre organisation, vous pouvez les ajouter à cette liste, en les séparant par des virgules.
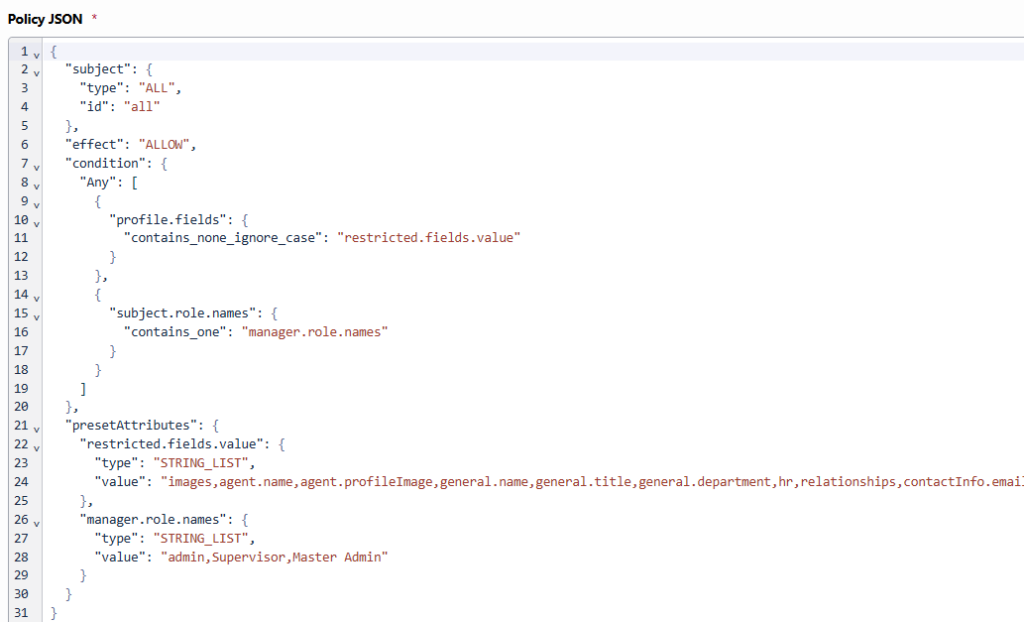
Ce modèle contient une règle Any, ce qui signifie que la politique renvoie le résultat Allow si l'une des conditions spécifiées est remplie. Le modèle comporte par défaut les deux conditions suivantes.
Condition 1
"profile.fields": {
"contains_none_ignore_case": "restricted.fields.value"
Cette condition vérifie si le champ du profil de l'utilisateur en cours de modification ne figure pas dans la liste des attributs prédéfinis de restricted.fields.value et ignore la sensibilité à la casse dans la comparaison. Si le champ en cours de modification ne figure pas dans la liste, le résultat de cette condition est Vrai. Vous pouvez modifier la liste des attributs prédéfinis soit en tant que champs individuels, soit en tant que nom de section, soit une combinaison des deux, en fonction des besoins de votre environnement. Pour plus d'informations sur les attributs prédéfinis pris en charge, voir liste des valeurs des champs restreints.
Condition 2
"subject.role.names": {
"contains_one": "manager.role.names"
Cette condition vérifie si le sujet a un rôle qui figure dans la liste des attributs prédéfinis de manager.role.names. Si le sujet a l'un de ces rôles, l'action est autorisée.
Une fois que le modèle a été enregistré en tant que politique, vous pouvez tester la politique pour confirmer qu'elle fonctionne comme prévu. Dans l'exemple suivant, le sujet a le rôle d'administrateur et la demande est donc autorisée, même si le champ du profil (agent.name) figure dans la liste des champs restreints.

Créer une politique d'accès à l'aide de la fonction Créer une politique
Pour créer une politique d'accès à partir de zéro, procédez comme suit :
- Cliquez sur Admin.
- Sous People & Permissions, cliquez sur Access Policies.
- Cliquez sur Menu > Gestion des utilisateurs > Politiques d'accès.
- Cliquez sur Créer une politique.
- Saisissez le nom et la description de la politique.
- Spécifiez les champs domaine, entité et action en fonction des exigences de votre politique. Vous pouvez consulter les modèles préconstruits pour créer votre propre politique.
- (Facultatif) Autoriser l'activation immédiate de la politique en désactivant l'option Enable Policy. Vous pouvez activer une politique ultérieurement en la modifiant. Pour plus d'informations, voir Activer la politique d'accès.
- Définissez les sections sujet, effet et condition dans le JSON de la politique en fonction de vos besoins organisationnels. Remarque :
- Pour plus d'informations sur les champs utilisés dans le JSON de la politique, voir la section Définitions utilisées dans ABAC .
- Pour plus d'informations sur la liste des attributs prédéfinis utilisés dans Policy JSON, voir Restricted fields value list.
- Pour plus d'informations sur les attributs de la politique d'accès, voir Contrôle d'accès basé sur les attributs.
- Pour valider la syntaxe JSON, cliquez sur Validate Syntax dans l'onglet Validate Syntax. Corrigez les éventuelles erreurs de syntaxe et procédez à l'enregistrement de la politique. Si vous ne validez pas la syntaxe explicitement, Genesys Cloud la valide automatiquement lorsque vous enregistrez la politique. L'étape de validation syntaxique valide les éléments suivants :
- Si les champs obligatoires sont disponibles.
- Les attributs énumérés sont valables pour la cible spécifiée.
- Toutes les comparaisons d'attributs sont valables pour leurs types de données respectifs.
- Les noms d'attributs prédéfinis n'entrent pas en conflit avec ceux définis dans le système.
- Cliquez sur Sauvegarder.
- Pour vérifier si la politique fonctionne comme prévu, cliquez sur l'onglet Test Policy et fournissez un échantillon de données, puis cliquez sur Test Policy.
- Pour revenir à la page des politiques, cliquez sur Annuler.